 [German]In some cases it could be helpful to execute programs as System or Trusted Installer to avoid access denied conflicts. This blog post introduces two solutions for Windows 10.
[German]In some cases it could be helpful to execute programs as System or Trusted Installer to avoid access denied conflicts. This blog post introduces two solutions for Windows 10.
What's the problem?
Some registry entries or files could not be accessed/changed from users belonging to Administrator group, because the ownership is set to System or TrustedInstaller. In forums you will find the suggestion, to take ownership and grant full access using the Security property page or the commands takeown and icacls. While this works, it's a sub optimal solution.
Would it not be better, if you can access objects like registry entries or file and folders with System or TrustedInstaller privileges? Well that's possible, let's have a short look at the situation.
Working with System credentials using PsExec.exe
I came across this solution several years ago. I run the registry editor (regedit.exe) via Run as administrator, but I wasn't able to change some registry keys. My problem was, that I've used VMLite and Virtualbox on the same machine, and ended with USB support issues. I was in need to delete a registry key, but that was refused. I've discussed this issue long time ago within my German blog post VMLite/VirtualBox und der USB-Support.
Instead of tampering with access rights and take ownership of the key, I came across a smoother solution. The Sysinternals-Suite contains the program PsExec.exe, that can be run from command prompt. Using the command:
PsExec.exe -s -i regedit
enables us to rung registry editor with System privileges (the switch –s will force that). The switch –i requests an interactive mode for the program). The command has to be executed from an administrative command prompt windows (see Windows 10: Open command prompt window as administrator).
But that won't work with Explorer
What I used as a smooth solution to access registry keys owned by System could also be helpful to access files and folders owned by System. But there is a problem: Files and folders will be accessed via Windows Explorer (explorer.exe). And the solution provided above won't work for explorer.exe. An attempt to access an object via explorer will be rejected.
I've discussed this issue in 2011 within my German blog post Explorer als Administrator ausführen. The technical background: Windows Explorer is also used as Windows shell – and Windows has an internal rule that prevents executing explorer.exe with System user rights. But there is a simple solution: Use a third party file manager instead of explorer.exe and execute it with System privileges.
I prefer portable file managers like FreeCommander or Explorer++ for this purpose and use PSExec to grant System privileges.
Execute programs as TrustedInstaller, is that possible?
Some objects (registry keys and files/folders) are owned by TrustedInstaller – that's a security feature to protect Windows app folders and system files from being altered by users and malware. The PSExec trick won't allow access such objects and alter files, folders or keys.
I've discussed a solution in October 2016 within my German blog post Programme als System oder TrustedInstaller ausführen. There is a free program, called PowerRun, from sodrum.org, that could be used for that purpose. Martin Brinkmann has also introduced this tool within this English article.
During writing a book about Windows 10 I decided back in January 2016 to test PowerRun again. But I failed to use PowerRun under Windows 10 – so I couldn't execute a program as TrustedInstaller. The reason was simple: Windows Defender and Smart Screen filter blocked this tool as malicious. I wasn't able to download and unpack PowerRun under Windows 7 and Windows 10. Although I'm sure, PowerRun isn't malicious, this solution is dead. I tested a few other tools (RunAsSystem and RunFromToken), but have had other issues.
Use Process Hacker and a Plugins
Finally I came across a Process Hacker forum thread from 2015. There are some hints how to execute a program as TrustedInstaller.
- You need Process Hacker (see SourceForge.net) – I used the portable version offered here (just unpack the archive into a local folder).
- Download also the TrustedInstaller plugins, mentioned within this forum thread. Unpack the zip archive and copy the .dll files to the appropriate 32/64 bit plugin sub folders.

After preparing ProcessHacker in that way, it's simple to execute a Win32 program using the steps below.
1. Launch ProcessHacker using the Run as administrator to grant administrative privileges.

2. Open ProcessHacker menu Hacker and select the command Run as trusted installer.
3. Enter the command into the dialog box Run as trusted installer – use Browse button to select the .exe file and confirm it via OK.
ProcessHacker launches the TrustedInstaller services and hands over the process, that needed to be run with TrustedInstaller privileges. The process will be executed with Autority [NT-Autorität\System], as it is shown below in Sysinternals Process Explorer.

This works with registry editor and with portable file managers like Explorer++. It allows me, to alter system files without obtaining ownership and granting full access rights. So I can change things without leaving traces in ownership and access rights. Maybe it's helpful for others.
Similar articles
Win10 Wiki
Windows 10: Open command prompt window as administrator
Uninstalling 'uninstallable' Windows Updates
Tip: Tools SetACL and Delproof2 now are free for commercial use
heidoc.net and 'Windows und Office ISO Download Tool' – an update
Bugs in Windows Disk Management tool
Tool test: MiniTool Partition Wizard Free

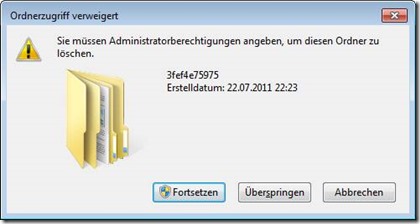



After launching explore++r as trusted installer, getting an error : error creating process with trusted installer. object name was not found
Thank you so much!!! Worked perfectly for me!!!
New tool from Winaero:
https://winaero.com/download.php?list.2 => ExecTI
Explorer++ crashes in Windows 10 problem:
https://explorerplusplus.com/forum/viewtopic.php?f=2&t=1755
FreeCommander XE, on the other hand, is fully Win10 compatible unlike explorer++
I have managed, in the past, to run an application as TrustedInstaller using vanilla Process Hacker. I don't remember exactly how I managed it, but I believe it requires you to have a TrustedInstaller process running already. This solution seems like it could be much easier to execute.
As the developer of the TrustedInstaller plugin writes in his forum thread (linked above):
You can also manually create processes with TrustedInstaller privileges without installing this plugin:
#1: Select the Services tab and start the TrustedInstaller service.
#2: Go back to the Processes tab and right-click TrustedInstaller.exe
#3: In the context menu, select the Miscellaneous > "Run as this user…" menu item.
Thank you very much for this tip! I used the procedure to get a script file correctly running in Task Manager.
FYI: PowerRun v1.3 worked just fine for me on Windows 10 1809 box.
In order to delete a file or folder which is owned by TrustedInstaller.exe, you have to take the rights of the files or folders with full authorization.
It's the wrong approach! Why should it take the rights of trustedinstaller.exe, if there are other ways? It's an additional security risk, just to mention.
The best tool for run as trustedinstaller is PowerRun
https://www.sordum.org/9416/powerrun-v1-3-run-with-highest-privileges/
I've gotten Explorer to run as ti with power run. For that matter the system in general. You disable windows defender /smartscreen (not so defense or smart but that's another article)
Right click Explorer, click open with, click power run and enjoy. Your screen will have a back background as it loads the system profile. You should now be running with NT Authority privileges. The question is how to do this by default.