![]() [German]Users of the Windows client for the Messenger service Telegram may be infected with a Miner that is mining Monero and Zcash crypto money.
[German]Users of the Windows client for the Messenger service Telegram may be infected with a Miner that is mining Monero and Zcash crypto money.
Malware authors have used a zero-day vulnerability in the Windows client for the telegram instant messaging service to infect users with cryptographic malware, as researchers at Kaspersky Lab announced today. See Securelist for details and preliminary information from Bleeping Computer.
Information from Kaspersky
The zero-day vulnerability has now been closed. But Kaspersky researcher Alexey Firsh says that cybercriminals apparently used the vulnerability for months before he discovered it in October 2017. According to Firsh, the zero-day vulnerability is in the implementation of the way the telegram Windows client handles the RLO (right-to-left override) Unicode character. This character switches between RTL and LTR text display.
Masked image with JavaScript
Firsh says that criminals trick telegram users with spam messages containing file attachments. The file names contain the RLO character that changed the text output direction directly in the middle of the file name. For example, the criminals sent a file called "photo_high_re*U+202E*gnp. js"to users in a campaign, where *U+202E* is the RLO sign.
If the filename was displayed on the screen, the last part of the filename was inverted and the file appeared as "photo_high_resj. png" (see screenshot)
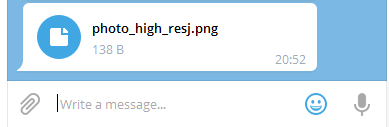 (Source: Bleeping Computer)
(Source: Bleeping Computer)
If the users wanted to open the file, they executed a JavaScript file instead of loading the supposed image. This started to download and install malware on the system.
Crypt-Miner and malware distributed
In the campaigns Firsh was able to track down, the crooks used the telegram Zero-Day vulnerability to install malware that secretly mines crypto money on users' computers. Monero, Zcash and Fantomcoin were mined.
Frish also discovered cases where criminals installed a backdoor Trojan (controllable via the telegram API) and other spyware tools. But in most cases, the malware authors focused on providing crypto-mining malware.
Comes from Russia
The zero-day vulnerability is not really innovative and is based on an old trick that has been known for at least half a decade and was first described in a 2013 F-Secure report. According to Firsh, Zero-Day was of limited use and was only used by a Russian malware author. "It seems that only Russian cybercriminals knew of this vulnerability, with all the fraud we have discovered in Russia,"Firsh writes in a report that was made available to Bleeping Computer before the release.
"We also discovered a lot of artifacts that indicated the involvement of Russian cybercriminals in carrying out a detailed investigation of these attacks," the expert said."We do not have accurate information about how long and which versions of the telegram products were affected by the vulnerability,"Firsh added. "What we do know is that usage in Windows clients began in March 2017."





