![]() [German]A new version of MegaCortex Ransomware is being distributed by malware such as Emotet. The new version not only encrypts the system's files but also changes the user's password.
[German]A new version of MegaCortex Ransomware is being distributed by malware such as Emotet. The new version not only encrypts the system's files but also changes the user's password.
The MalwareHunter team has been able to access corresponding malware examples. In the following tweet they point to a corresponding message to victims.
The latest MegaCortex ransomware also threats to leak files: "[…] downloaded your data […]. In the unfortunate event of us not coming to an agreement we will have no choice but to make this data public."
Of course, it can be a lie, but for sure they could do it.@demonslay335 pic.twitter.com/lWgJnSDykS— MalwareHunterTeam (@malwrhunterteam) November 5, 2019
After encrypting files, this is a new quality – the user is virtually locked out of the user account under Windows. In addition, the blackmailers threaten to make the data public if it is not paid for. Bleeping Computer has taken up this case here. After an analysis by Vitali Kremez and Bleeping Computer, the MegaCortex ransomware changes its behavior.
- In the new version of the Ransomware, the files are provided with the file name extension .m3g4c0rtx after encryption.
- The Ransomware changes the Windows password of the logged-in user so that the user can no longer log in.
- A message "Locked by MegaCortex" is now displayed on the login page with an e-mail account stating that the computer has been locked by the malware.
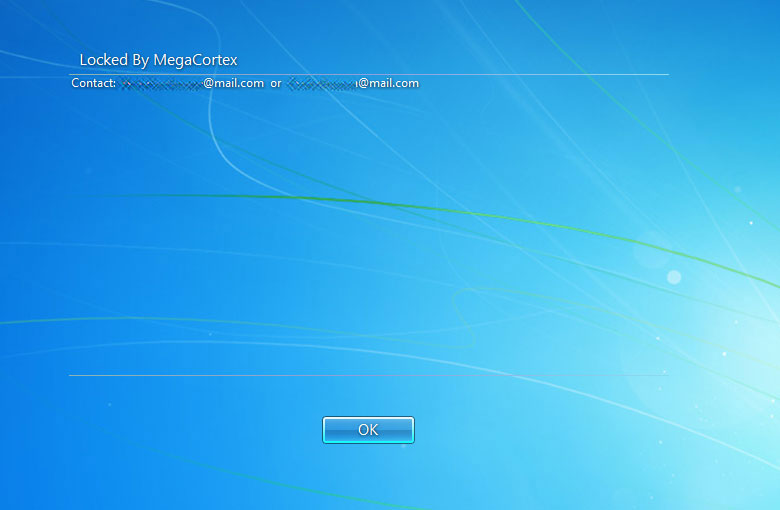
(MegaCortex notification, Source: Bleeping Computer)
In addition, the attackers claim to have uploaded the victim's data to a secure location. The following text appears in the express message.
"We have also downloaded your data to a secure location. In the unfortunate event of us not coming to an agreement we will have no choice but to make this data public.
Once the transaction is finalized all of copies of data we have downloaded will be erased."
The text contains the threat to publish the data in case of non-payment. So far it has not been confirmed whether attackers have actually uploaded files of the victims to their own servers. If a data outflow can be confirmed, affected persons are not only confronted with the problem of being victims of a Ransomware attack. Depending on the information copied, this may also be a data protection violation that must be reported in the EU.
If the main launcher is executed by MegaCortex, it extracts two DLL files and three CMD scripts to C:\Windows\Temp. Then the actions are executed by the Ransomware. The launcher currently has a Sectigo certificate for an Australian company called MURSA PTY LTD. In the meantime, Sectigo has declared the certificate invalid. Further details on the course of the attack can be found in the Bleeping Computer article.





