 [German]Smartphone vendor Gigaset published a document names Lösung Malware-Angriff Smartphones on April 8, 2021, that should help to cleas Android phones infected by malware since April 1, 2021. In the following text, I will compile and comment the information given from Gigaset and supplement it with my own findings, enriched with the many questions that remain unanswered here. After that, every owner of Gigaset devices should decide how to proceed.
[German]Smartphone vendor Gigaset published a document names Lösung Malware-Angriff Smartphones on April 8, 2021, that should help to cleas Android phones infected by malware since April 1, 2021. In the following text, I will compile and comment the information given from Gigaset and supplement it with my own findings, enriched with the many questions that remain unanswered here. After that, every owner of Gigaset devices should decide how to proceed.
Malware attack on Gigaset Android devices
In the blog post Lösung Malware-Angriff Smartphones, the manufacturer writes that some older smartphones had problems with malware, which was noticed during routine control analyses. According to the manufacturer's statements, the "infection of smartphones was stopped on April 7, 2021." I was able to prove the first infections in the article German Gigaset Android Update Server probably delivers malware on April 1, 2021.
Which models are not affected?
According to Gigaset's statement, the smartphone models of the smartphone series GS110, GS185, GS190, GS195, GS195LS, GS280, GS290, GX290, GX290plus, GX290 PRO, GS3 and GS4 are not affected by this malware attack.
But here the question is open, what about the Gigaset GS280. I refer to the German comment by Bolko, who writes: Also, at least the GS280 is missing from the list of affected devices, or should the 51 files with 19.93 MB. each be normal?
These models are potentially affected
According to Gigaset, only older smartphone models from the GS100, GS160, GS170, GS180, GS270 (plus) and GS370 (plus) series are potentially affected. I interpret this as being tied to the update server used – one of which, according to Gigaset, was affected by a supply chain attack and delivered malware via an auto-updater present in the firmware.
Note: It's now becoming a bit clearer to me – it looks like historically two update providers (#1 Redstone, #2 Adups) were/are used by Gigaset to update. On older devices, a system updater from Redstone is in use in the firmware and from those, a server was presumably compromised. The system updates come from Gigaset Germany and Poland, but are executed via the update servers in China (which act as providers). What is unclear to me: Why can third parties so easily provide packages to an update server and this is not noticed? Is it not digitally signed, or has a private key for signing been lost?
Not all devices affected, update missing?
Feedback from readers and my experience with my own devices show that not all copies of the above models were infected. Gigaset writes about this:
According to current information, only some devices from the affected product lines were infected, where the software updates provided by Gigaset in the past were not executed by the user. Malware was uploaded to these devices via a compromised server of an external update service provider.
Unfortunately, the manufacturer remains tight-lipped about the details of the "provided software updates". In the blog post Preliminary analysis of Gigaset malware attack through auto-installer in firmware, I had pointed out that security researchers also refer to the auto-installer com.redstone.ota.ui installed in the firmware of Gigaset Android smartphones as Android/PUP.Riskware.Autoins.Redstone. That would be the system updater of the provider Restone. Here, it would have been good to know which component (com.redstone.ota.ui or update.apk, etc.) should have been installed. Blog reader Bolko raises the same questions in this German comment that run through my head.
That an uninstalled software update was missing and this enabled the infection, I can't rule out. But I don't want to leave the manufacturer's statement uncommented. The statement could be interpreted as if the user refused an update (to put it mildly). This is vehemently contradicted in this German comment (and in feedback I received from other users). It could also simply be that the manufacturer's update approaches don't work and people never got those updates. I'll refer you to this German comment from blog reader Niklas, who points out the problem with the manufacturer's statement:
We have about 110 Gigaset GS370 Plus in use. All controlled via a mdm. There all options for app installation are blocked far from the apps I have enabled.
No apk sideload
No playstore
No installation via any path.Only the update mechanism of the firmware has still been open.
If the (security) update was provided by Gigaset as an app via Google Play Store or APK side-load and not as a firmware update, the Gigaset devices would not be suitable for management via Mobile Device Management (MDM). The question remains open here whether user errors or a failure of the update mechanism led to the current problems. In any case, it can be determined that the Restone system updater is removed by the system updates that have now started.
Problem: Third-party update server
At this point, I point out a problem that is nonchalantly paraphrased as "update server of a provider" in the whole issue. According to the comments on this German Gigaset blog post, the GS3 and GS4 models use update servers from ADUPS Ltd. The Shanghai-based Chinese company does offer update services for a billion devices. You can pretend that, but a company like Gigaset should also make the selection from reliability points of view. And that's where problems are looming, according to my knowledge so far.
The provider ADUPS LTD. has enjoyed a reputation for years that is anything but "clean slate". I found the German heise article Adups: Android-Riskware mit Déjà-vu-Effekt, which does not really leave a good feeling if this is the provider that manages Gigaset device updates. Since there was a malware attack on Gigaset devices in 2019 (see the following note) that presumably involved the previous provider Redstone, and their update servers have presumably now been compromised again in a supply chain attack and delivered the malware, that doesn't paint a good picture of the matter either.
Note: Which also, at least for me, raises question marks on my forehead: after all, this is not the first incident of Gigaset devices being infected by malware rolled out via update servers (see this German article from 2019). Moreover, I refer to this German comment here within my German blog, which states that Gigaset models are marketed as Kaan N series in the Turkish-speaking region. There has been a malware infestation there in August 2020, my Turkish is lousy, so I could not evaluate the details yet.
Malware infection should be cleaned automatically
In a preliminary conversation by phone a few days ago, Gigaset stated that they had stopped the infection of the update server, that no new malware would be delivered anymore, and that they had even provided a solution in cooperation with the provider that affected devices would clean themselves automatically. This is what Gigaset's announcement reads like:
Gigaset took immediate action and contacted the update service provider. The latter took immediate action and confirmed to Gigaset that the infection of smartphones could be stopped on April 7.
Measures have been taken to automatically rid infected devices of the malware.
To do this, the devices must be connected to the Internet (WLAN, WiFi or mobile data). We also recommend connecting the devices to the charger. Affected devices should be automatically freed from the malware within 8 hours.
At this point, there is at least some doubt that this works for all users (whether it does not work for anyone, I cannot answer). The German comment here does confirm that malicious apps are gone – but browser redirects in Google Chrome still happen. In addition, I refer at this point this German comment from April 8, 2021, which was received on my article at heise. Just opening the Google Play Store was enough to receive the following alert message.
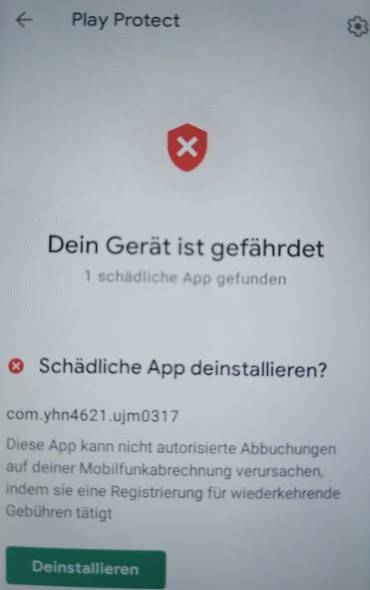
So it can be said: The automatic immunization of the devices is not always as reliable as Gigaset claims. In addition, I have my doubts, a compromised device that sends data (e.g. via WhatsApp) and whose shutdown I had recommended (Malwareangriff: Was Gigaset Android-Gerätebesitzer jetzt machen sollten) is allowed back on the network. What you can currently do as an affected person if you want to get involved in the auto-update:
- Remove the SIM card from the device, and uninstall WhatsApp as well as SMS to prevent messages from being sent during the update phase.
- Connect the device to a charger, as the update process can take up to 8 hours, log the booted device into the guest access of a WLAN router if possible and let it update.
- Afterwards, install an antivirus app to at least be informed about possible malware.
- Treat WhatsApp and SMS messages with all caution, as there is a risk of reinfection due to the incident.
I hope that these measures will at least prevent the biggest crap during the auto-update. How Gigaset's instructions for manual cleanup look, and why that does not always work or works very poorly, I covered in part 2 of this article series. There, I also address what else needs to be considered.
Similar articles:
German Gigaset Android Update Server probably delivers malware
Update on malware attack on Gigaset Android devices (April 6 2021)
Preliminary analysis of Gigaset malware attack through auto-installer in firmware
Malware infection of Gigaset Android devices: Analyses and options for action (April 8/9. 2021) – Part 1
Malware infection of Gigaset Android devices: Analyses and options for action (April 8/9. 2021) – Part 2





