[German]Microsoft had to admit on begin of July 2023 that suspected Chinese hackers from the Storm-0558 group were able to forge security tokens using a stolen private MSA key. Then then gain broad access to Microsoft cloud services, as Wiz now revealed. So it's not just about the ability to access accounts at Exchange Online and Outlook.com, which Microsoft had admitted recently.
[German]Microsoft had to admit on begin of July 2023 that suspected Chinese hackers from the Storm-0558 group were able to forge security tokens using a stolen private MSA key. Then then gain broad access to Microsoft cloud services, as Wiz now revealed. So it's not just about the ability to access accounts at Exchange Online and Outlook.com, which Microsoft had admitted recently.
Previously known: Outlook account hack
A suspected China-based hacking group, named by Microsoft as Storm-0558, had succeeded in June 2023 in gaining access to email accounts of about 25 organizations stored in the Microsoft Cloud. These include government agencies (U.S. State Department), as well as corresponding private accounts of individuals likely associated with these organizations. That has been confirmed by Microsoft.
The background was that the attackers came into possession of a private (MSA) customer key for Microsoft accounts. This MSA key could be used to generate (forge) security tokens. But these security tokens could not only be used for private Microsoft accounts (e.g. Outlook.com). Due to bugs in the Azure services code, the security tokens were not verified correctly and allowed access to Azure AD accounts (now called IntraID accounts).
Microsoft had officially admitted this, but downplayed the incident – I had reported on it in the blog post China hackers (Storm-0558) into Microsoft's cloud, Outlook Online accounts hacked. In another post Follow-up to the Storm-0558 cloud hack: Microsoft is still in the dark, I reported more details made public by Microsoft.
Microsoft has declared the MSA key (and other keys) invalid and fixed the bugs in the code of the Azure services. Subsequently, it could also be observed that the attackers switched to other methods. But Microsoft admitted in an article that until now it was unknown how the group called Storm-0558 could get hold of the MSA key used internally at Microsoft (and actually inactive) in the first place.
Broad access to Azure AD possible
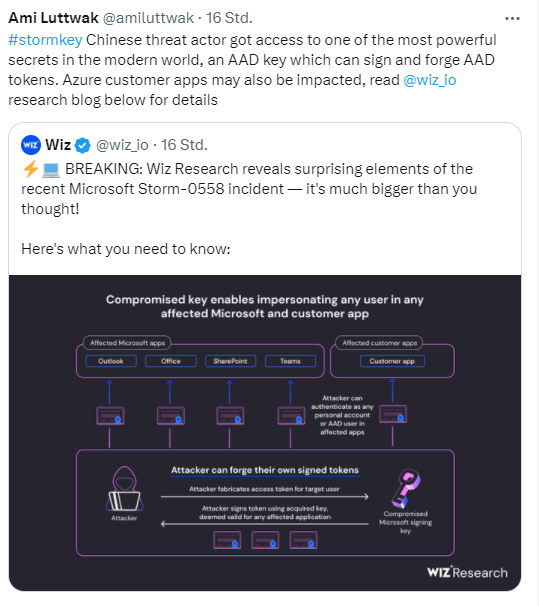
Now security researchers from Wiz have made public that the incident was even more explosive than Microsoft even admitted. The following tweet from Ami Luttwak, CEO and founder of Wiz, reveals this.
The key message is that the Microsoft Storm-0558 incident is much more serious than previously known. The Chinese threat actor had gained access to an AAD key that can be used to sign and forge AAD tokens. This means Azure customer applications may also be affected. In a series of follow-up tweets, details known to Wiz security researchers are revealed. The details can also be read in this Wiz blog post.
While Microsoft reports that threat actors compromised Exchange Online and outlook.com, the actual scope of the compromised applications was much broader, the security researchers write. That's because Wiz Research took a closer look at the latest security incident. They found that the compromised Microsoft key is a "skeleton key" that can be used for Microsoft's MSA tenant in Azure. This not only opens up access to outlook.com and Exchange Online, but also opens Pandora's box wide open. Because the key could also be used to generate security tokens for Azure applications. This is what Witz wrote:
The compromised Microsoft signing key potentially allows the threat actors to forge access tokens for ALL Microsoft's personal account services and any Azure Active Directory (AAD) applications supporting both multi-tenancy and Microsoft's OpenID v2.0 implementation.
It means that all applications that use the "Log in with Microsoft" feature could be affected as well. If you want to see the whole potential disaster, you can read this Wiz blog post.
What can admins do?
It can be assumed that the Storm-558 hackers only targeted selected accounts on outlook.com and Exchange Online. But it can never be ruled out that other Azure AD accounts (Azure AD is now called EntraID) were compromised as part of this action as a precaution. The following image provides an overview of what types of applications may have been affected.
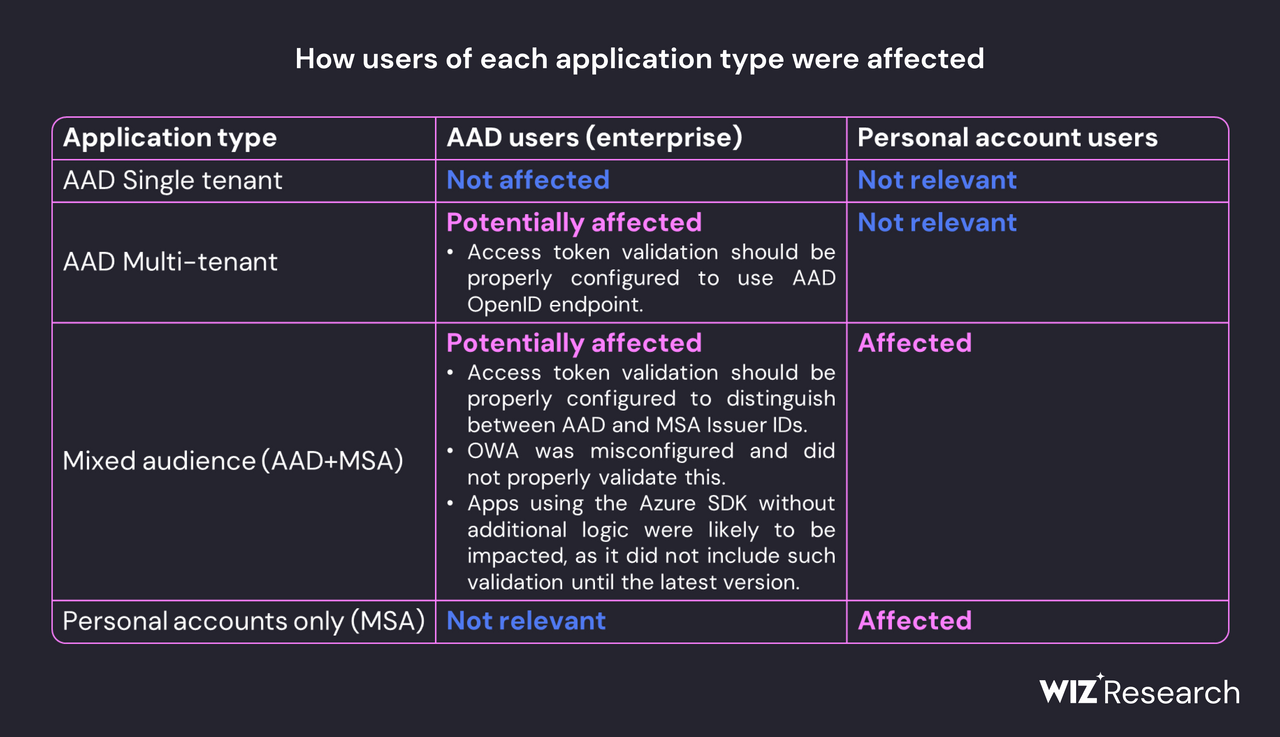
Affected application types; source: Wiz
This includes Azure Active Directory applications (EntraID applications) that support "Microsoft personal accounts only" and work with Microsoft Protocol v2.0 that may be affected. This includes managed Microsoft applications such as Outlook, SharePoint, OneDrive and Teams, as well as customer applications that support Microsoft account authentication (including applications that allow the "Log in with Microsoft" feature).
But it also potentially affects any Azure Active Directory application that supports "mixed audience" (or multi-tenant) and works with Microsoft protocol v2.0. This is because the threat actor could forge valid access tokens and impersonate application users who had logged in with their personal Microsoft account.
Administrators should therefore review application access logs to ensure that these accounts are not affected by Storm-0558. For more prevention and early detection tips, see this Wiz blog post.
Similar articles:
China hacker (Storm-0558) accessed Outlook accounts in Microsoft's cloud
Follow-up to the Storm-0558 cloud hack: Microsoft is still in the dark
After CISA report on Storm-0558 hack, Microsoft provides customers with enhanced cloud logging