 [German]Recently, there was a warning to customers of the telephone system provider 3CX who have integrated an SQL database into the software for CRM purposes. I reported on the issue in the blog post 3CX warning: Disable SQL database integrations (Dec. 15, 2023). Users of the 3CX software complained about the slow processing of the early reported security vulnerability. One user subsequently contacted me by email because the response to criticism in the provider's forum was very specific: The posts were deleted. And the reader's account was also blocked – but the whole thing can be recapitulated, which I have done below.
[German]Recently, there was a warning to customers of the telephone system provider 3CX who have integrated an SQL database into the software for CRM purposes. I reported on the issue in the blog post 3CX warning: Disable SQL database integrations (Dec. 15, 2023). Users of the 3CX software complained about the slow processing of the early reported security vulnerability. One user subsequently contacted me by email because the response to criticism in the provider's forum was very specific: The posts were deleted. And the reader's account was also blocked – but the whole thing can be recapitulated, which I have done below.
Background information on 3CX
3CX is a software development company and developer of the eponymous 3CX telephone system software. It is a complete business communication system that includes phone calls, video conferencing, live chat, Facebook and the integration of incoming WhatsApp messages. The company was founded in 2005 and, according to Wikipedia, has around 200 employees (as of 2018).
On the one hand, the 3CX telephone system software appears to be in wider use. On the other hand, 3CX 2023 has attracted attention due to two security vulnerabilities (see links at the end of the article). The slow processing of a security vulnerability in the 3CX MySQL integration (see blog post 3CX warning: Disable SQL database integrations (Dec. 15, 2023)) has led to anger among various users – as I have noticed from reactions from administrators on Facebook.
3CX forum: Criticism not welcome
Blog reader Jörn V. contacted me by email before Christmas because he had noticed the VE-2023-4995 vulnerability and then followed the case in the 3CX forums. There has been a Security Vulnerability – SQL Integration thread on the topic since December 15, 2023. It may be helpful for some users to go through the forum posts.
Jörn informed me, that on Friday, December 15, 2023, two critical posts appeared in response to the new vulnerability. Shortly afterwards, the two posts disappeared.

In the screenshot above, I have shown the current timeline as an excerpt between several posts. Now, there may well be reasons why posts are (or have to be) deleted. The blog reader pointed out. that the deleted entries has been saved by the Internet Archive using a snapshot – the result can be viewed here. The following screenshot shows this passage.

I can't see anything ad hoc that could justify deletion. In my blog post, I also addressed the fact that the timeline from the discovery of the vulnerability to 3CX's response was by no means flattering for the company. And the question should also be asked as to why a CERT could not reach a company like 3CX for 45 days.
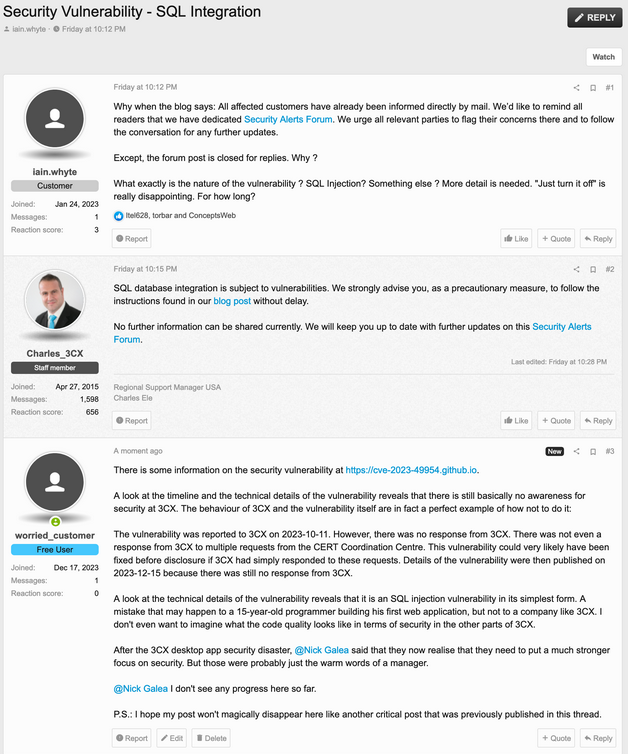
The disappearance of the posts then motivated the reader to also write a post on the topic (see screenshot above). You could now guess what happened: After two hours, this post also disappeared again.
The reader concluded that 3CX apparently does not like critical voices on the subject. But it gets even more remarkable, as the reader found out. Jörg wrote that 3CX (presumably in response to critical voices in the forum in the past) changed its forum rules some time ago to the effect that you can only post there as a customer with a 3CX subscription.
Free account and license blocked
The reader had used an account based on a 3CX Free Subscription (which no longer exists and was only possible for "existing customers") to post his contribution. After 3CX deleted the post, the reader's account was of course immediately blocked in the forum on the grounds of "SPAM".
The reader still had an email from Nick Galea (3CX CEO) personally in his mailbox, which was saved for the now blocked account. The content of the mail was as follows:
Please find another product to use rather then our free license.
regards,
Nick galea
The reader assumes, that Nick Galea has allegedly personally canceled the free subscription for the account and suspects that the criticism has hit the CEO. The reader enumerates the last 3CX security disaster (supply chain attack on the 3CX desktop app, see my links at the end of the article) and the new incident.
3CX security initiative just vapor ware?
The reader referred to the post Actions not words – Our 7 Step Security Action Plan! by Galea in April 2023, in response to the supply chain attack. At the time, it was supposed to be a major turnaround in terms of security at 3CX. In the above context, however, it doesn't look to me as if the CEO really wants to follow up with action.
The reader comments: "I think other users of 3CX should also be able to get an impression of how 3CX really stands on the subject of security and how critical voices on the subject are dealt with." What's your opinion?
Similar articles:
3CX desktop app (probably) infected in a supply chain attack (March 29, 2023)
Additional information about the compromised 3CX desktop app
3CX warning: Disable SQL database integrations (Dec. 15, 2023)





