[German]After I had been researching on the "suspected case" of the AnyDesk hack for a week, which was confirmed as a "successful cyberattack" on Friday, February 2, 2024, the BSI finally published a notification with TLP:CLEAR on February 5, 2024. The threat level is classified as "2 / Yellow" – as of January 29, 2024, this was still classified as TLP:Amber-Strict. Here is a brief summary of what the BSI is telling its readers.
[German]After I had been researching on the "suspected case" of the AnyDesk hack for a week, which was confirmed as a "successful cyberattack" on Friday, February 2, 2024, the BSI finally published a notification with TLP:CLEAR on February 5, 2024. The threat level is classified as "2 / Yellow" – as of January 29, 2024, this was still classified as TLP:Amber-Strict. Here is a brief summary of what the BSI is telling its readers.
AnyDesk was hacked
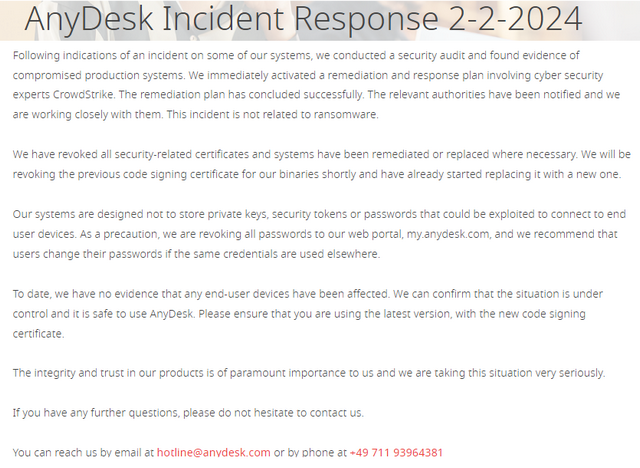
The facts: The provider of the remote maintenance software AnyDesk has fallen victim to a hack that also affected the production systems. The provider rules out ransomware, but confirms that attackers were on the move in its systems. We don't know when and we don't know what was or is affected. What the provider AnyDesk has openly disclosed, I have prepared in the article AnyDesk confirmed, they have been hacked in January 2024, Production systems affected – Part 1. Here is the official thin communication from the provider (incidence report from AnyDesk) in the screenshot.
I have been aware of this since Friday, February 2, 2024, 22:44. Up to this point, there was only one notification from the BSI classified as TLP:Amber-Strict, as far as I know (I haven't seen it), dated January 29, 2024, which went to a small circle of recipients in the area of critical infrastructures. Because of this classification, these recipients were not allowed to pass on the document or speak outside the circle of addressees.
Disclosure of the CERT GER (BSI) dated February 5, 2024
In the meantime, readers have pointed me to today's BSI publication on the topic. It is classified as TLP:Clear and can be accessed here.

There you can see that the BSI has removed any classification – probably because "public sources" reported on the incident – and AnyDesk made this public last Friday. Ultimately, the BSI confirms what was known: AnyDesk Software GmbH – manufacturer of the widely used remote access and screen sharing software of the same name – has published a press release about an attack involving the compromise of internal systems.
We learn that the BSI is in contact with the company and can confirm the incident (what a bull shit, it has been confirmed by AnyDesk on Feb. 2, 2024). The interpretation is also interesting: "Public sources report that source code and certificates for signing the software were also leaked in the course of this compromise" – the abbreviation [BLEEP2024] stands for the article by Bleeping Computer.
AnyDesk carried out the clean-up and restoration directly together with a service provider. As part of this, certificates were withdrawn and updates were provided to replace the certificates for end users. According to information provided by Anydesk Software GmbH to the BSI, the following certificate, among others, will be replaced:
Zertifikat-Seriennummer: 0DBF152DEAF0B981A8A938D53F769DB8
AnyDesk has also thoroughly checked the source code and was unable to detect any manipulation, it says. AnyDesk Software GmbH told the BSI that the company currently has no positive knowledge of a compromise of user data. However, AnyDesk has forced a password reset of the customer portal my.anydesk.com as a precautionary measure. I wrote something about the last sentence in part 5.
The German CERT's (BSI) assessment
With a yellow rating, the BSI has set the warning level quite low. According to the BSI's assessment, there is a risk that this information could be used for further attacks on the provider's customers due to the possible outflow of source code and certificates. According to the BSI, man-in-the-middle and supply chain attacks are conceivable in this context.
In particular, the certificates that may have been leaked could have gone unnoticed or, in the worst case, attacks that have already taken place could have remained undetected. The measures implemented by the operator have considerably reduced the current risk potential. Nevertheless, it cannot be ruled out that malicious versions of the software signed with the compromised certificate will be offered by attackers on third-party sites or sent to customers in a targeted manner, writes the BSI.
In a corporate context, the application is often used with privileged rights, which opens up a particular risk potential. With regard to possible effects on critical infrastructures and administration, the BSI believes that the incident described can affect these in a similar way and have the consequences described.
The BSI's recommendation
The BSI recommends cautious use of the software, especially with updates or permanently open connections. In addition, the manufacturer's recommendation should be followed to install the latest version with the new certificate. Updates should only be obtained via the update function within the software or via the manufacturer's website.
In addition, employees (especially those who are mainly in contact with the company or the software) should be made aware of this in their own company, along with the advice that software should never be obtained from insecure sources. The manufacturer also recommends a precautionary password change, especially if the access data used with AnyDesk is also used with other services. I have already written about these issues in my subsequent blog posts.
Small conclusion
First the BSI notification from the end of January 2024 was "TLP AMBER:STRICT" – now there is an assessment of "warning level yellow" – and people should be careful. Simply replace the AnyDesk client to the most recent version and that's it? Nice, I'm curious to see whether the replacement works.
I will report on the experiences and consequences of the incident in the blog in more posts. To close the circle: Even with the BSI notification and notifications from other agencies that were brought to my attention via the readership, we still don't know when the hack took place and what exactly was compromised at AnyDesk or what was leaked. But I "think" we "officially" have just restored cyber security.
Articles:
AnyDesk confirmed, they have been hacked in January 2024, Production systems affected – Part 1
AnyDesk hack undercover – more information and thoughts – Part 2
AnyDesk hack undercover – Suspicious cases and more – Part 3
AnyDesk hack undercover – Access data offered for sale – Part 4
AnyDesk hack – A review – Part 5
AnyDesk hack – Review of the German CERT BSI report – Part 6
AnyDesk hack – Notes on exchanging certificates for Customs clients 7.x – Part 7
AnyDesk hack – more details (FAQ from Feb. 5, 2024) – Part 8
AnyDesk hack already noticed on December 20, 2023? – Part 9
AnyDesk hack confirmed as of December 2023; old certificate recalled – Part 10
AnyDesk hack: Revoke chaos with old certificates? – Part 11
AnyDesk hack: Newly signed clients available; what are your experiences? – Part 12
Similar article:
Störung bei AnyDesk, jemand betroffen?
AnyDesk: Be careful in using that remote support software