[German]Luca Casonato already pointed out an issue in connection with Chromium browsers on July 9, 2024. In the browser, all Google websites are granted full access to system data such as CPU usage, GPU utilization, memory usage and processor information via a hidden extension. Allows Google sites to provide detailed information about the system, which enables fingerprinting. Furthermore, this information can also benefit Google during debugging. This would be a violation of the Digital Markets Act (DMA). I'll extract the relevant information in a blog post.
[German]Luca Casonato already pointed out an issue in connection with Chromium browsers on July 9, 2024. In the browser, all Google websites are granted full access to system data such as CPU usage, GPU utilization, memory usage and processor information via a hidden extension. Allows Google sites to provide detailed information about the system, which enables fingerprinting. Furthermore, this information can also benefit Google during debugging. This would be a violation of the Digital Markets Act (DMA). I'll extract the relevant information in a blog post.
Notes from readers
This topic has already been brought to my attention by two readers in recent days. Marcel had already emailed me on July 10 with the information that the Google Chrome browser is spying even more on its users and monitoring them. This would also affect other browsers that are based on Chromium, such as Brave or Microsoft Edge. The function is hidden in the browser extensions, where the user cannot see it.
Reader Norddeutsch also raised the question "Chrome Edge, Brave – additional user identification hidden?" in the discussion area and mentioned that the browser contains a hidden "Chrome extension" that Google can use to query information on memory consumption, GPU & detailed CPU information.
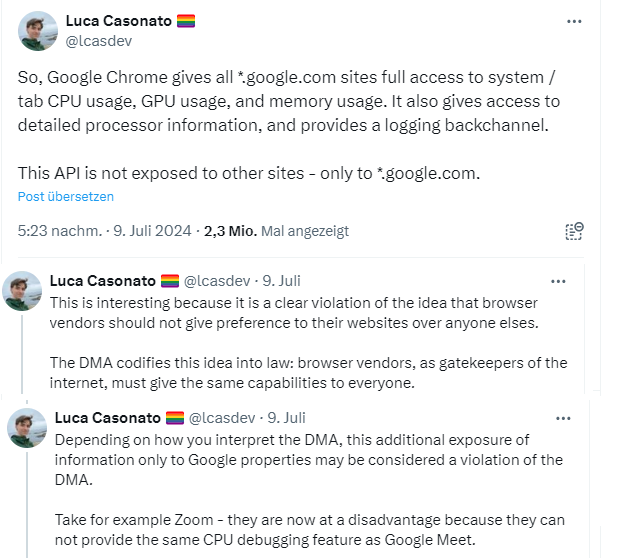
Source: A tweet from Luca Casonato
Both readers' comments refer to the following tweet by Luca Casonato on Platform X, which has caused quite a stir. The tweet was viewed 2.3 million times.
The tweets state that Google Chrome gives all *.google.com websites full access to the CPU, GPU and memory usage of the system or tab. The browser also allows access to detailed processor information and provides a feedback channel for logging. This API is not accessible for other websites – only for *.google.com, writes Casonato.
He sees a clear violation of the idea that browser manufacturers should not favor their websites over others. Luca Casonato writes that, depending on how one interprets the DMA, this additional disclosure of information only for Google properties can be seen as a violation of the DMA. He cites Zoom as an example. Its developers are at a disadvantage because they cannot offer the same CPU debugging function as Google Meet.
Built into extension, other browsers also affected
Luca Casonato states that the whole thing was implemented via a built-in Chrome extension that cannot be deactivated and is not displayed in the extension bar. The source code of this Chrome extension can be viewed in the Chromium project. In further posts, the discoverer writes that this function is also available in Microsoft Edge exclusively for *.google.com domains. He then adds that the Brave browser behaves in exactly the same way as Chrome and Edge.
The extension that allows Google to retrieve this information exclusively from *.google.com is also pre-installed in Brave. Brendan Eich responded on X, pointing to this image where it says that the extension is enabled in Brave to ensure that Google Meet works properly.
Additional information
Bolko pointed out in a separate comment that it was the integrated extension "Hangout_services" with the extension ID: nkeimhogjdpnpccoofpliimaahmaaome. This has been around since at least 2016. Google can use this extension to query the following information:
"permissions": [
"desktopCapture",
"enterprise.hardwarePlatform",
"processes",
"system.cpu",
"webrtcAudioPrivate",
"webrtcDesktopCapturePrivate",
"webrtcLoggingPrivate"
whereby this is only accessible for the pages https[:]//*.google[.]com/*. This is used by Google Meets (meets[.]google[.]com), for example. Bolko adds that this code is also available in the Supermium browser:
supermium-124-pre\\chrome\\browser\\resources\\hangout_services\\manifest.json
would be included. The ungoogled Chromium project has also adopted the code. However, this extension is not activated for the two browsers Supermium and ungoogled Chromium. This is because the ID mentioned above does not appear when the following command is entered:
chrome://serviceworker-internals/
According to Bolko, you can use the GN flags in the flags.gn file to set which functions are to be activated or deactivated in the generated binary before compiling:
enable_hangout_services_extension=false
github[.]com/ungoogled-software/ungoogled-chromium/blob/master/flags.gn
I did a quick search – in this article, the editors of Golem refer to a blog post by Simon Willison, who writes that this system information has been available since October 2013. On ycombinator, a Google employee who does not work for the Chromium project writes that there is a simple explanation. Developers can view the system load per browser in Google Meet when debugging.
Addiendum: A reader mentioned, that you can block all extensions via GPO and only whitelist desired extensions. The question has arisen that in this case, the extension should be blocked – but I have not tested this.