[German]Microsoft security experts have discovered a ransomware campaign targeting VMware ESXi instances. Via an Auth Bypass vulnerability (CVE-2024-37085) it is possible to gain full administrative privileges on domain-joined ESXi hypervisors. The vulnerability is being exploited by several ransomware operators to attack ESXi installations.
[German]Microsoft security experts have discovered a ransomware campaign targeting VMware ESXi instances. Via an Auth Bypass vulnerability (CVE-2024-37085) it is possible to gain full administrative privileges on domain-joined ESXi hypervisors. The vulnerability is being exploited by several ransomware operators to attack ESXi installations.
Discovery by Microsoft
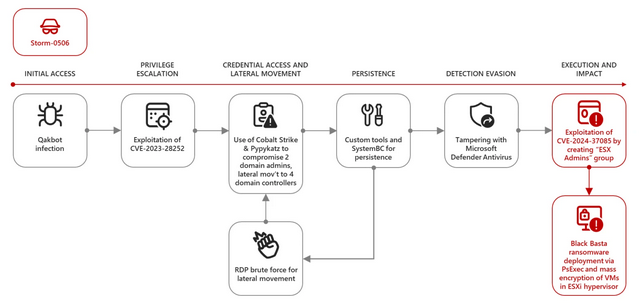
In 2023, Microsoft security researchers have observed that ransomware actors have targeted ESXi hypervisors to enable mass encryption with a few clicks. Microsoft states that groups such as Storm-0506, Storm-1175, Octo Tempest, Manatee Tempest and other ESXi encryption programs such as Akira, Black Basta, Babuk, Lockbit and Kuiper have been observed. It also showed that ransomware operators are constantly innovating their attack techniques to increase the impact on the organizations they attack.
Microsoft security researchers have recently discovered a vulnerability in ESXi hypervisors that is already being exploited by several ransomware operators. In a ransomware attack, full administrative privileges on an ESXi hypervisor can be gained via the vulnerability. This allows the threat actor to encrypt the file system, which can affect the executability and functionality of the hosted servers. In addition, the threat actor can access hosted VMs and potentially exfiltrate data or move laterally in the affected network.
Analysis of the vulnerability CVE-2024-37085
VMware ESXi is a bare-metal hypervisor that is installed directly on a physical server and provides direct access and control over the underlying resources. Virtual machines can be set up in VMware ESXi hypervisors. Important servers in a network (AD servers, etc.) are also often virtualized via ESXi.
Source: Microsoft
While analyzing attacks, Microsoft security researchers have discovered a technique for exploiting the CVE-2024-37085 vulnerability used by ransomware groups such as Storm-0506, Storm-1175, Octo Tempest and Manatee Tempest in numerous attacks. In several cases, the use of this technique led to Akira and Black Basta ransomware deployments.
The attack technique involves the execution of the following commands, which leads to the creation of a group called "ESX Admins" in the domain and the addition of a user to this group:
net group "ESX Admins" /domain /add
net group "ESX Admins" username /domain /add
The threat actors can use this command to exploit the vulnerability in domain-joined ESXi hypervisors to escalate privileges on the ESXi hypervisor and gain full administrative access. Further analysis of the vulnerability revealed that VMware ESXi hypervisors that are joined to an Active Directory domain grant full administrative access by default to any member of a domain group called "ESX Admins".
This group is not a built-in group in Active Directory, which does not exist by default. ESXi hypervisors do not check to see if such a group exists when the server joins a domain, and will continue to treat all members of a group with that name as having full administrative access, even if the group did not originally exist. In addition, membership in the group is determined by name and not by security identifier (SID). Microsoft researchers have identified three methods to exploit this vulnerability:
- Add the "ESX Admins" group to the domain and add a user to this group
- Rename any group in the domain to "ESX Admins" and add a user to the group or use an existing group member
- Updating ESXi hypervisor privileges, because even if the network administrator designates another group in the domain as the management group for the ESXi hypervisor, the full administrative privileges for members of the "ESX Admins" group are not immediately removed and can be abused
This finding was reported to VMware in early 2024. Microsoft recommends that organizations using domain-joined ESXi hypervisors apply the security update released by VMware to address the CVE-2024-37085 vulnerability. Furthermore, in the article Ransomware operators exploit ESXi hypervisor vulnerability for mass encryption, Microsoft provides information on guidelines that also help companies to protect their network from attacks. According to this article, the US security authority CISA warns companies about the vulnerability and gives authorities three weeks to patch ESXi instances.