 [German]A German blog reader recently shared an observation from his IT department with me. An employee was bombed by a veritable wave of spam mail (more than 1,000/hour). All the emails had some kind of confirmation for a registration, which aroused my suspicions.
[German]A German blog reader recently shared an observation from his IT department with me. An employee was bombed by a veritable wave of spam mail (more than 1,000/hour). All the emails had some kind of confirmation for a registration, which aroused my suspicions.
What the reader reported
The blog reader reported that an employee from the HR department had been bombarded by over 1,400 emails within an hour. The CheckPoint solution used in the company did not catch everything, and the volume of SPAM emails was brutal.
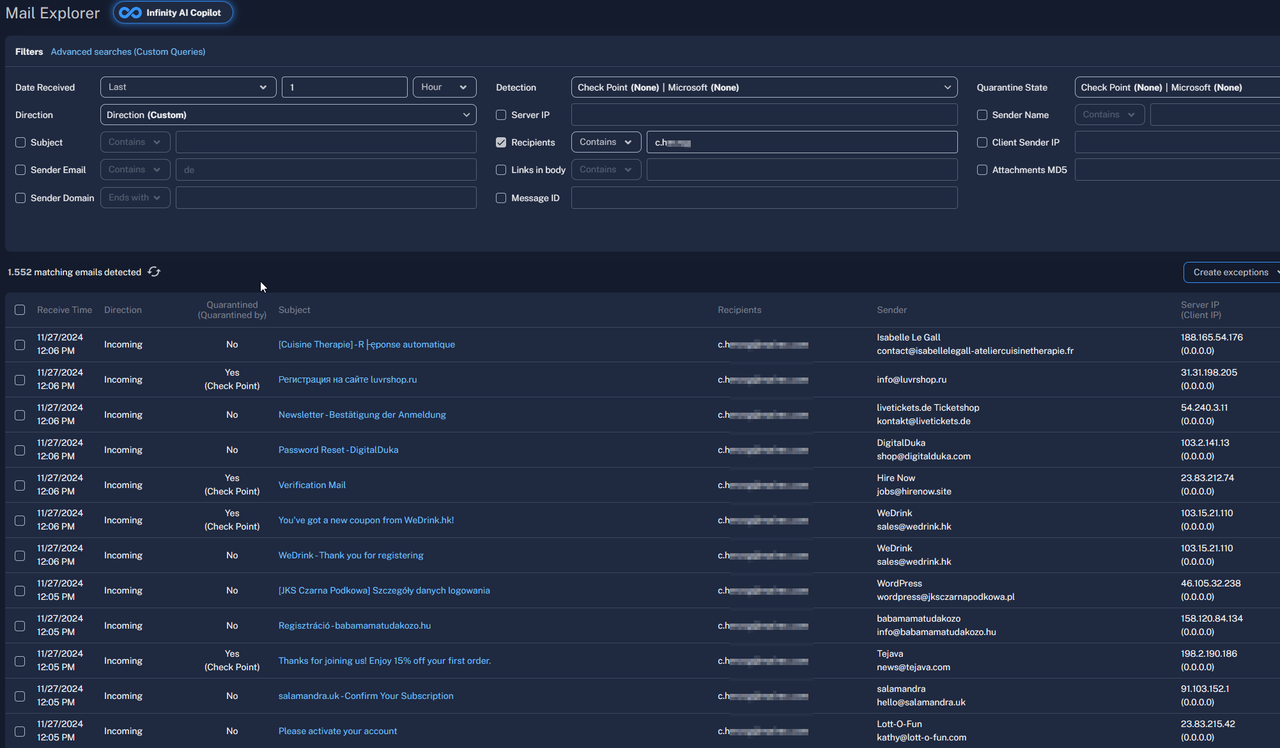
Spam mails; Click to zoom
He sent me the screenshot shown here and asked whether other readers had also reported this – which I have to deny. The reader then removed the email address in question from the Exchange Online so that there was no more spam.
The reader wrote that he had never experienced such a mass of SPAM in the company, especially as the IT department maintains the DMARC, DKIM, SPF records etc. properly and uses a CheckPoint solution for filtering.
My suspicion: Something shall be hidden
I have to go back a while and refer again to my German blog post Massen-Newsletter-Spam und der Paypal-Konten-Hack. One user reported that one of his customer was being spammed with newsletter registrations (just like in the picture above). Within hours, thousands of emails (newsletter registrations, contact form responses) from a wide variety of sources arrived in his mailbox.
There are spambots on the move that exploit/antest contact forms on websites and misuse them to send spam. This is well known (the CGI script formmail.pl is abused to send spam).
And at the end of the day, the whole thing turned out to be a hack of the affected user's PayPal account. The flood of SPAM messages was intended to prevent the user from seeing the warning messages about unauthorized access to the PayPal account – these were hidden among the many SPAM messages.
Additions from the reader
I had pointed out the above issue to the reader. He said in his reply that it was quite possible that it was not a huge or widespread attempt to phish credentials or SPAM, but rather a targeted action.
He has traced some sender IP addresses. It seems to him that the accounts of some bulk mail providers have been or are still being hacked. Many of the SPAM mails had come from MailChimp, MailChannels or SendGrid. He has filed an abuse report with these providers.
Regarding the suspicion of an account hack, he writes that the employees in the company are also quite trained and have a certain level of vigilance. The person concerned had not disclosed their access data or company account data anywhere during the days/weeks. The security solutions with MDR and SOC in the mail stream had not detected anything either.
Mentions at reddit.com
The reader then searched for something along the lines of "disguising attacks with SPAM" and found what he was looking for on reddit.com. He subsequently wrote that the SPAM could come from the Black Basta ransomware group.
Case #1 on reddit.com
In the reddit.com thread End Users getting email bombed, an administrator also described the above problem about a month ago. Some users from his company were bombarded with thousands of spam emails from various websites. The person asked if anyone knew of a good way to prevent this.
In the thread, another user confirms that this has also been the case for him recently. During the email bombing, users received an audio call from external third parties claiming they were from the IT department and needed to remote into the systems to fix the issue.
This user confirmed that this attack has also been used in the past to prevent people from seeing a legitimate email alerting them to a scam in progress.
This type of attack is difficult to block because it is a subscription attack. The email account is subscribed to news groups, newsletters, etc. from legitimate services around the world. Sometimes you can catch some of the SPAM through filtering rules.
Case #2 on reddit.com
A blog reader pointed out a second reddit.com thread Weird Spam influx + teams calls?? Help, which was created two months ago and describes something similar. He is inundated with spam emails, but can't block them all because they come from everywhere and have nothing in common (he started blocking languages and countries).
Other users also confirm this observation and mention that the aim is often to distract the victim from something else.
Black Basta tactics for attacks
At reddit.com somebody linked to the blog post Ongoing Social Engineering Campaign Linked to Black Basta Ransomware Operators by Rapid 7 from May 2024. The security researchers describe that Rapid7 had identified an ongoing social engineering campaign targeting several managed detection and response (MDR) customers at the time.
The threat actor (dubbed Black Basta) floods a user's email inbox with junk mail and then calls the victim to offer help. The attacker prompts affected users to download remote monitoring and management software such as AnyDesk or use Microsoft's built-in Quick Assist feature to connect remotely.
Once a remote connection is established, the threat actor downloads payloads from the user's infrastructure to intercept the affected user's credentials and use the affected user's access for intrusion. In one case, it was also observed that the attacker used Cobalt Strike beacons on other resources within the attacked network. Details can be found in the linked article.



