[German]A short information for administrators of Windows Server systems. In December 2024 Microsoft has released patches for LDAP vulnerabilities, that that allows attackers to run an DoS attack on Active Directory. Now a Poor of Concept has been released, that shows, that these vulnerabilities allows an attacker to crash any unpatched Windows Server.
[German]A short information for administrators of Windows Server systems. In December 2024 Microsoft has released patches for LDAP vulnerabilities, that that allows attackers to run an DoS attack on Active Directory. Now a Poor of Concept has been released, that shows, that these vulnerabilities allows an attacker to crash any unpatched Windows Server.
A first hint
I first came across the following tweet days ago, which was prepared by Darkreading in the article Unpatched Active Directory Flaw Can Crash Any Microsoft Server.
Security researchers from SafeBreach have analyzed the DoS vulnerability CVE-2024-49113 (Windows Lightweight Directory Access Protocol (LDAP) Denial of Service Vulnerability, CVSS index of 7.8). This vulnerability was discovered together with Remote Control Execution (RCE) vulnerability CVE-2024-49112 (CVSS index of 9.8) in Active Directory's Lightweight Directory Access Protocol (LDAP).
Microsoft has closed both vulnerabilities with the December 2024 security updates. The problem is that one of the two critical Active Directory Domain Controller vulnerabilities not only enables the originally reported denial of service (DoS) attacks. The vulnerability can also be used to crash unpatched Windows servers. Experts fear that many companies are still running unpatched Windows servers and are vulnerable to such attacks.
There is a zero-click exploit
There is already an exploit for the vulnerability, as I read here. Security Online outlines in the article PoC Exploit Released for Zero-Click Vulnerability CVE-2024-49113 in Windows how the unpatched vulnerability can be exploited. Blog reader Andy Wendel had notified me on Saturday, 4. January 2024, in a private messsage on Facebook about this topic.
Andy wrote "very ingenious post about a now closed CVE-2024-49112" and linked to the following tweet, which picks up on the post LDAPNightmare: SafeBreach Labs Publishes First Proof-of-Concept Exploit for CVE-2024-49113.
Nothing really new, except that there is a proof of concept. However, Andy Wendel gave me some more information on Facebook, which I am posting 1:1 for the readership. He notes:
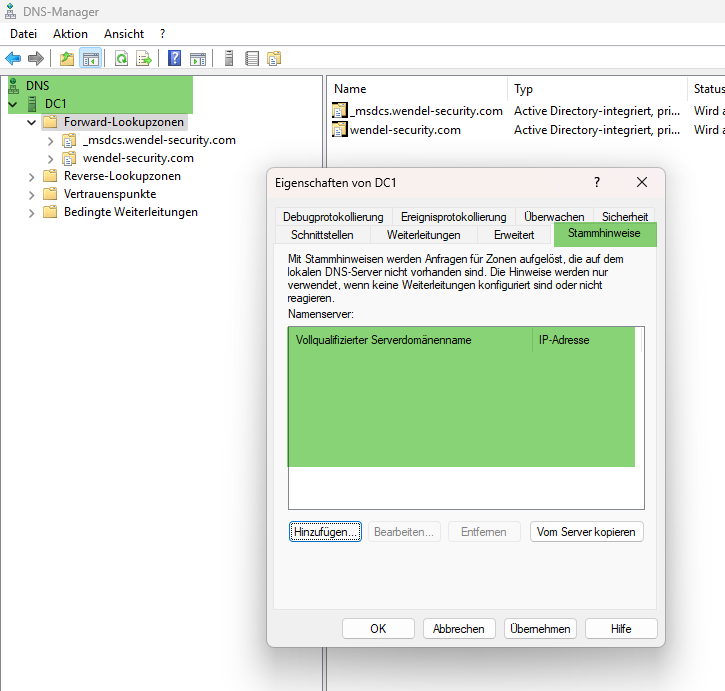
I always recommend: domain controllers should never be able to resolve externally with the DNS server – ever. In addition, they should have deleted all root servers.
Andy has provided the following screenshot, which shows the properties of a DC in the DNS Manager.
He wrote that this was shown to him years ago by the security consultant of the company @yet, Thomas Peters. He notes: "the recursion should be deactivated" (see following screenshot).
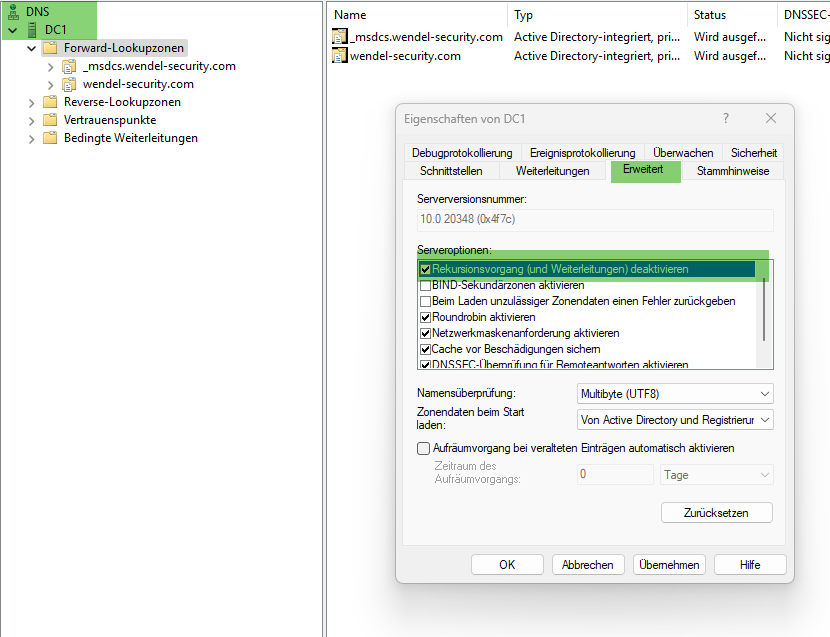
He commented "You are welcome to use my information with the screenshots etc." (thanks to Andy) – maybe it will help some of the readers.
Similar articles:
Microsoft Security Update Summary (December 10, 2024)
Patchday: Windows 10/Server Updates (December 10, 2024)
Patchday: Windows 11/Server 2022/2025-Updates (December 10, 2024)
Patchday: Windows Server 2012 / R2 (December 10, 2024)
Patchday: Microsoft Office Updates (December 10, 2024)
Critical LDAP vulnerability in Windows (CVE-2024-49112)