[German]A small addendum from the last few weeks. On April 11, 2025, Microsoft announced that support for ActiveX components would be deactivated by default in Microsoft 365 (i.e. Office 365).
[German]A small addendum from the last few weeks. On April 11, 2025, Microsoft announced that support for ActiveX components would be deactivated by default in Microsoft 365 (i.e. Office 365).
Active X background
ActiveX is the term for a (somewhat outdated) software component model from Microsoft for active content. ActiveX components extend Microsoft's Component Object Model (COM) standards under Windows. Under Windows, ActiveX components are usually compiled in DLL or OCX files.
Use in IE, Visual Basic and VBA (Office)
ActiveX was a big thing in Internet Explorer, with the COM-capable web browser new functionalities could be mapped in the browser using ActiveX objects. In addition to the now "discontinued" Internet Explorer, ActiveX components were used in Visual Basic and in VBA under Office.
ActiveX as a security risk
ActiveX technology was regarded as a walking security risk, as the developers of the components had to guarantee their security. This is because the ActiveX component model did not provide any security functions of its own. The ActiveX components also do not run in isolation in a sandbox.
ActiveX has therefore long been discontinued as a Microsoft technology. In the fall of 2024, I mentioned in the article Windows Legacy DRM deprecated; ActiveX diasbled in Office 2024 that ActiveX support will disappear in Microsoft Office 2025.
ActiveX will be disabled by default in MS 365
On April 11, 2025, Microsoft announced in the Techcommunity article ActiveX disabled by default in Microsoft 365 the plans to disable ActiveX by default in Microsoft 365 applications.
ActiveX is a powerful technology that enables extensive interactions within Microsoft 365 applications. However, as its deep access to system resources also increases security risks, Microsoft has decided to take action.
From April 2025, the Windows versions of Microsoft Word, Microsoft Excel, Microsoft PowerPoint and Microsoft Visio will have a new default configuration for ActiveX controls that will disable all controls without notification.
Change default settings
The previous default setting "ActiveX controls: Ask before enabling all controls with minimal restrictions" allowed users to enable potentially dangerous ActiveX controls that could be exploited by attackers through social engineering or malicious files. With the new default setting "ActiveX controls: Disable all controls without notification" will make Office components more secure by completely blocking these controls, reducing the risk of malware or unauthorized code execution.
![]()
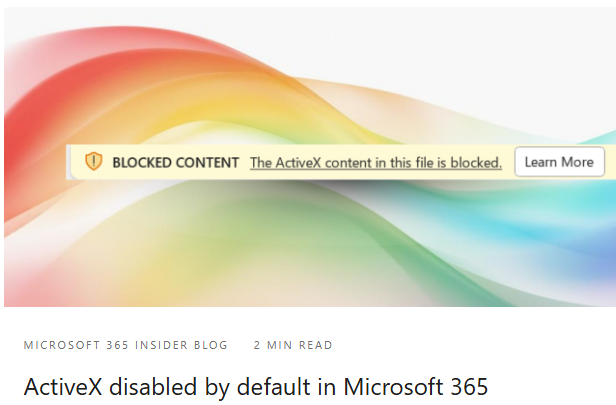
If users open a file in one of the Office applications mentioned that contains ActiveX controls, the above message is displayed in a yellow banner. The ActiveX content in this file is blocked.
Microsoft notes that this message is only displayed if the ActiveX settings in the Trust Center are not set manually before this default change. If ActiveX is generally disabled, users can no longer create or interact with ActiveX objects in Microsoft 365 files. However, some existing ActiveX objects are still displayed as a static image. But it is not possible to interact with them.
Activate ActiveX again
If ActiveX is required, the user can activate it manually. To do this, select File > Options > Trust Center and then the Trust Center Settings button in the Office application. In the Trust Center dialog box, the ActiveX settings option can be set to Ask before enabling all controls with minimal restrictions and confirmed by clicking OK.
Administrators can control the behavior in the Group Policy Editor by selecting Group Policy Path > User Configuration > Administrative Templates > Microsoft Office 2016 > Security Settings > Disable All ActiveX > Disabled. Details can be found in this support article.
Rollout in stages
This feature is available to all Beta channel users and will be rolled out to Current Channel (Preview) users on version 2504 (build 18730.20030) or later.