[German]A short warning to blog readers who use the iVentoy tool to distribute operating system images via a network and a PXE server. There is currently a discussion that the tool (currently version 1.0.2) installs an insecure kernel driver and an obscure certificate under Windows. As long as this point has not been properly clarified, I can only advise you to "keep your hands off this tool". Addendum: The developer has already reacted and released version 1.0.21.
[German]A short warning to blog readers who use the iVentoy tool to distribute operating system images via a network and a PXE server. There is currently a discussion that the tool (currently version 1.0.2) installs an insecure kernel driver and an obscure certificate under Windows. As long as this point has not been properly clarified, I can only advise you to "keep your hands off this tool". Addendum: The developer has already reacted and released version 1.0.21.
What is iVentoy?
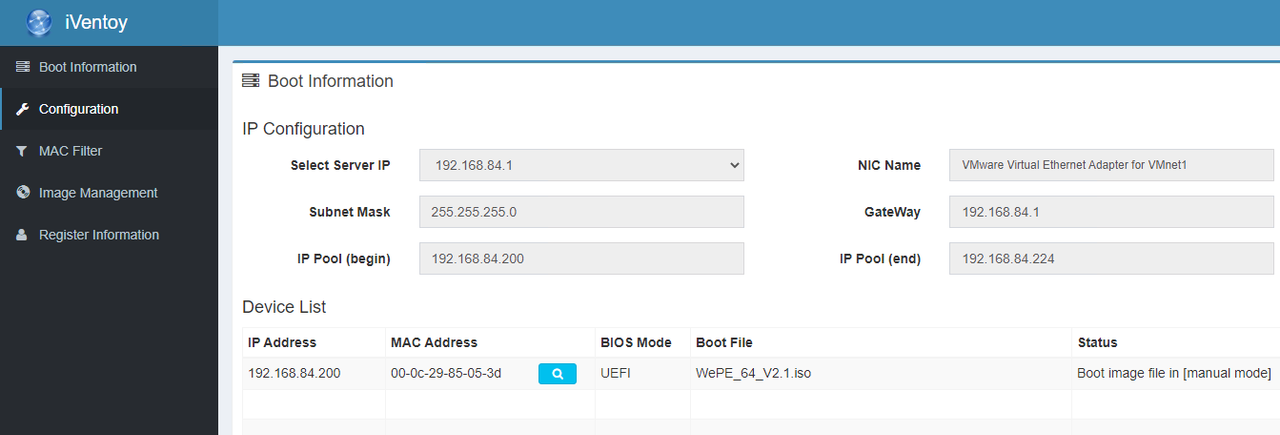
iVentoy (not to be confused with Ventoy, which can create USB boot sticks for operating system installation) is a tool for distributing operating system images over a network.
The project's website states that iVentoy is an extended version of the PXE server, which can be used to boot and install operating systems on several computers simultaneously via the network.
iVentoy is extremely easy to use, without complicated configuration. The administrator simply places the ISO file with the installation image in the specified location and selects PXE boot in the client machine. The operating system image (or installation image) is then loaded and executed on the client via the network by PXE-Boot.
iVentoy supports x86 Legacy BIOS, IA32 UEFI, x86_64 UEFI and ARM64 UEFI mode at the same time. iVentoy supports more than 110 common variants of operating systems (Windows/WinPE/Linux/VMware) according to the website.
Background information: The main developer and maintainer of the Ventoy project is Hailong Sun, also known as longpanda. Longpanda is also the developer of iVentoy.
Discussion about security issues
Benedikt contacted me via email (thanks) and pointed me to the reddit.com post iVentoy tool injects malicious certificate and driver during Win install (vulnerability found today) from May 6, 2025. The thread starter writes that he just came across a report about a vulnerability in iVentoy. Ventoy is known for its very useful tool for creating bootable USB devices.
Security problem found in iVentoy
On GitHub there is the current entr iVentoy installing unsafe Windows Kernel drivers #106, which deals with the problem. It states that iVentoy 1.0.2 can be downloaded from the GitHub page and is installing unsafe Windows Kernel drivers via the following archives.
iventoy-1.0.20-linux-free.tar.gz, iventoy-1.0.20-win32-free.zip, iventoy-1.0.20-win64-free.zipAll these archive files contain the entry \data\iventoy.dat. The .dat file is decrypted to \data\iventoy.dat.xz at execution time by the iVentoy app in RAM. The creator of GitHub entry #106 wrote a Python script to analyze the decrypted result and came to no positive result.
VirusTotal and Defender alerts
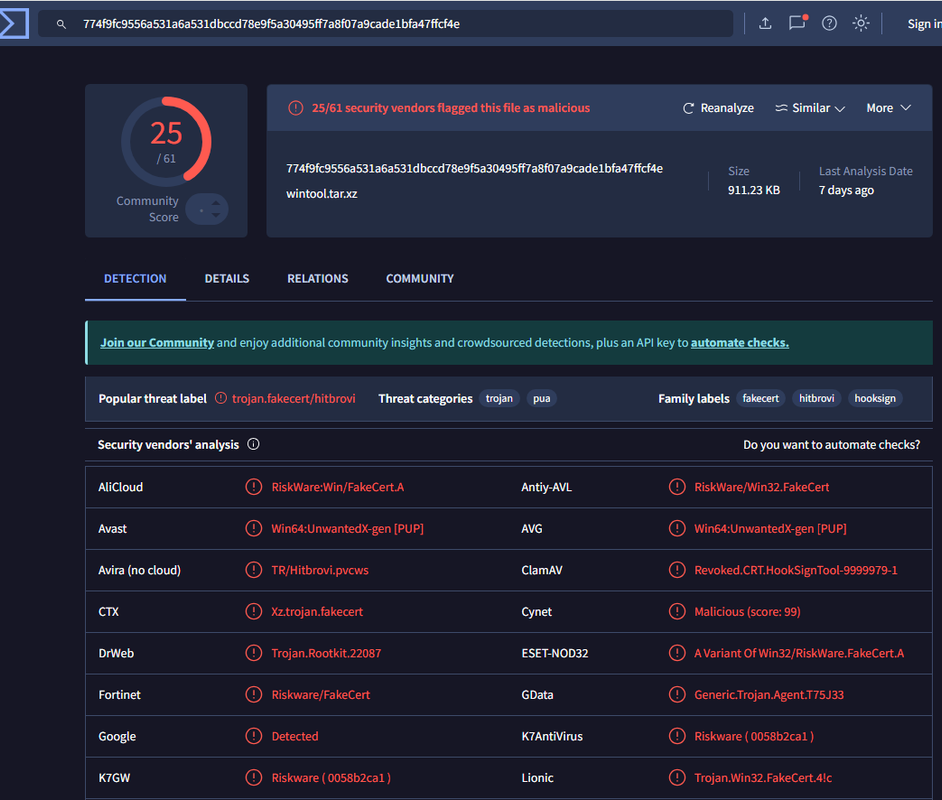
When the decrypted iventoy.dat.xz is opened with 7zip, some of the extracted files are found listed with positive results on Virustotal.com and Windows Defender. The file iventoy.dat.xz\iventoy.dat.\win\wintool.tar.xz probably contains an obscure certificate, which Virustotal identifies as "malicious".
It also says that the analysis of "iventoy.dat.xz\iventoy.dat.\win\vtoypxe64.exe" shows that it contains a self-signed certificate with the name 'EV' certificate "JemmyLoveJenny EV Root CA0" at offset=0x0002C840 length=0x70E. And it says that iVentoy installs insecure Windows kernel drivers.
A warning from Talos
This certificate rings all the alarm bells, because in 2023 Talos-Security published the article Old certificate, new signature: Open-source tools forge signature timestamps on Windows drivers with a warning.
Cisco Talos has observed threat actors exploiting a Windows policy vulnerability that allows the signing and loading of unsigned kernel-mode drivers with a signature timestamp prior to July 29, 2015. According to Talos, the actors use several open-source tools that change the signing date of kernel-mode drivers. The goal is to load malicious and unverified drivers signed with expired certificates into Windows.
Cisco Talos security researchers have observed more than a dozen code-signing certificates with keys and passwords in a PFX file hosted on GitHub and used in conjunction with these open source tools. The post also mentions the above certificate.
Most of the drivers that Talos was able to identify contained a Simplified Chinese language code in their metadata. This points to Chinese native speakers as the authors. Cisco Talos wrote in 2023 that they had also identified a case where one of these open source tools was used to re-sign cracked drivers to circumvent digital rights management (DRM).
Cisco Talos had published a second blog post showing the real abuse of this vulnerability by an undocumented malicious driver called RedDriver. I had reported on the scenario in July 2023 in the article Windows: Malware still loadable in kernel drivers (RedDriver attack).
Take care when using (also Ventoy)
At this point I would say "be careful, using iVentoy" – and also Ventoy (which contains also blobs) in older versions. Shortly, after I've published the German edition of this blog post, iVentoy 1.0.21 has been released. The iVentoy developer has released an official statement about the above suspicions:
OK. Let me explain about this.
iVentoy is a tool to install Windows/Linux through PXE. As we know, PXE is based on network, so we need a driver to mount the ISO file in the server side as a local drive (e.g. Y: Z:) though network. So I choose httpdisk.
httpdisk is an open source project
https://www.accum.se/~bosse/httpdisk/httpdisk-10.2.zip
httpdisk driver will only be installed in the WinPE step, that means it only exist in the RAM and will not be installed to the final Widows system in the harddisk.
But in windows, by default a driver file must be signed to install.
So I find a signed version of httpdisk driver file in the internet and try to use it. But this signed version has already been rejected by latest Windows, so finally I use another way, to boot the WinPE in test mode (again, only the WinPE environment).
When WinPE is booted in test mode, a driver file no need to be signed to install.So finally, actually we don't need the signed version of httpdisk driver file and don't need to load the CA anymore. Only that the code is not deleted.
So I will release a new version later that remove the signed httpdisk driver file and will not load the CA.