 [German]Travis CI is a very popular service among software developers, which is used to create and test many software projects. The service is part of the software supply chain of many software solutions. Moreover, Travis CI's credentials and login information are linked to popular cloud providers such as GitHub, AWS, Docker Hub, and many others. Team Nautilus, Aqua Security's research unit specializing in the cloud-native technology stack, has now discovered a vulnerability in the free version of the Travis CI API.
[German]Travis CI is a very popular service among software developers, which is used to create and test many software projects. The service is part of the software supply chain of many software solutions. Moreover, Travis CI's credentials and login information are linked to popular cloud providers such as GitHub, AWS, Docker Hub, and many others. Team Nautilus, Aqua Security's research unit specializing in the cloud-native technology stack, has now discovered a vulnerability in the free version of the Travis CI API.
This vulnerability potentially compromises more than 770 million logs of the Travis CI API – directly affecting the software supply chain of many software developers. This is because Travis CI access keys and credentials are linked to popular cloud service providers such as GitHub, AWS, Docker Hub and many others. Aqua Security has published a detailed blog post describing the vulnerability.
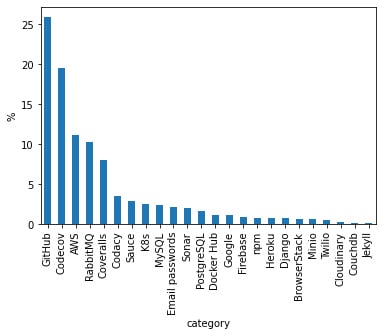
Service providers associated with clear-text tokens found in exposed Travis CI logs, Source: Aqua Security
Attackers can access historical plaintext logs through the vulnerability and use this sensitive data to launch massive cyberattacks and move laterally in the cloud. Some of these cloud service providers confirmed that up to 50 percent of the Travis CI tokens, user data and passwords shared with them were still valid and allowed access to their customers' accounts.
Known since 2015 – but still a serious problem
According to Travis CI, this issue was reported back in 2015 and most recently in 2019 and subsequently fixed. But as Team Nautilus' recent research clearly demonstrates, it is still a serious problem. Nautilus found that the valid range of logs is between 4,280,000 and 774,807,924, which means there are potentially more than 770 million compromised logs. The oldest logs are from January 2013 and the most recent are from May 2022.
Recommendation: Change the Travis CI API key immediately
This threat could lead to an increase in attacks on the software supply chain, an already critical issue. Although Team Nautilus also found potential access to restricted protocols, Travis does not currently plan to take any further action. As a result, Nautilus recommends changing all Travis CI API keys immediately. Aqua Security has communicated the vulnerability findings to the respective service providers. Almost all of them were alarmed and reacted quickly. Some of them initiated a comprehensive replacement of the keys.





