[German]I've been working on the "suspected case" of the AnyDesk hack since a week, which was confirmed as a "successful cyberattack" on Friday, February 2, 2024. At the weekend, I wrote up my findings in four articles (see links at the end of the article). I would now like to add a few more thoughts and tips for readers as a kind of follow-up.
[German]I've been working on the "suspected case" of the AnyDesk hack since a week, which was confirmed as a "successful cyberattack" on Friday, February 2, 2024. At the weekend, I wrote up my findings in four articles (see links at the end of the article). I would now like to add a few more thoughts and tips for readers as a kind of follow-up.
AnyDesk hacked
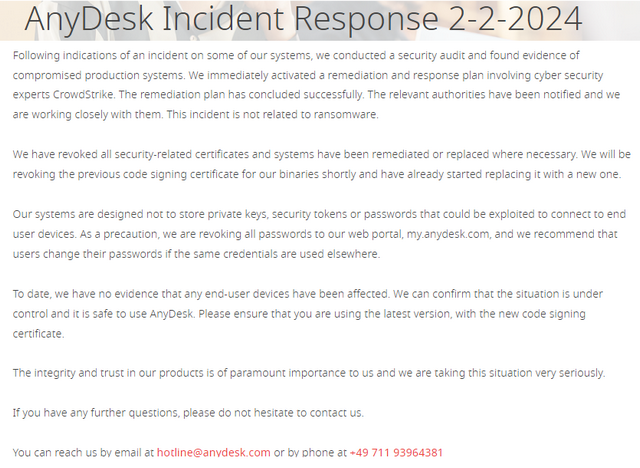
The provider of the remote maintenance software AnyDesk has fallen victim to a hack that also affected the production systems. The provider rules out ransomware, but confirms that attackers were on the move in its systems. I have prepared details in the article AnyDesk confirmed, they have been hacked in January 2024, Production systems affected – Part 1, as far as the provider has disclosed them, as well as some background information (from my point of view).
The screenshot above shows the AnyDesk incidence report again. I have prepared further information in other parts (see links at the end of the article). Below are some comments and information for my blog readership.
Disclosure Friday 10:44 p.m. CET?
The first point I would like to address concerns the process of disclosing the security incident. I had written something about the BSI warning in the article AnyDesk hack undercover – more information and thoughts – Part 2 – there may be good reasons for the whole thing – others have to evaluate. AnyDesk was hacked in January 2024, production systems affected – but I had outlined in AnyDesk confirmed, they have been hacked in January 2024, Production systems affected – Part 1, that I had been investigating the suspicion of a cyber attack for days.
I can understand that there was turmoil at AnyDesk, and great consideration is given to how and when the public is informed. But as of February 1, 2024, there was an offer from me to talk with the CEO about the incident, which did not happen all day on Friday, February 2, 2024. Okay, I'm not "the center of the world" and they have no obligation to talk to me at all and in a timely manner.
At some point on Friday late afternoon, I left the office and communicated this to AnyDesk. I had asked in the email for a brief categorization of who the cyber incident affects (on-premises hosting or cloud users) and what customers should or can do. They said "We'll do a press release today, we'll send it to you beforehand." I simply went to sleep at around 10:30 pm – and then saw at around 3:00 am on Saturday, Feb. 3, 2024 that an email with the above AnyDesk Incident Response 2-2-2024 had arrived at 10:44 pm on Feb. 2, 2024.
Security researcher Jake Williams picked up on it in the above tweet in his "Remarks on the AnyDesk incident". Original quote: This shouldn't be published on a Friday afternoon when the systems were taken offline days ago. This is a PR move. Companies that are transparent don't do this kind of nonsense.
Disclosure as a bad joke
I would like to focus again on another aspect that I noticed – I already mentioned it in the post AAnyDesk hack undercover – more information and thoughts – Part 2. The incidence report does not contain any information about when what happened. In general, the whole thing is simply a joke and PR bluster – admitting what can no longer be denied.
This leaves a lot of uncertainty for those affected and speculation for observers. Excerpt from AnyDesk's privacy policy: "The success of our products depends not least on our customers being able to trust in the security and protection of their data." That is a message and a promise.
Even if presumably no customer data was leaked when accessing the production systems at AnyDesk, i.e. no customer information is required by GDPR, this is anything but "good practice". At the time of writing this article, there is no indication on the AnyDesk website or on their cyber incident status page for visitors. You need to know the deep link to the report to be informed about the incident.
Jake Williams echoes the above thoughts in several tweets, writing that this behavior alone means one of two things:
- AnyDesk is not following good security practices for its own development environment,
- or the extent of this intrusion is much greater than anticipated..
Then, in the sequence of tweets shown above, he makes various recommendations to those responsible for AnyDesk as well as to every user of AnyDesk (although many do not know that they are users because AnyDesk comes in some software packages on the systems. Williams' outlined recommendations in the above tweet.
Users are left out in the cold
The case can be reduced to the headline above. Nobody knows exactly where to look and how far back in time to look at logs. At the moment, I can only see the following immediate measures for administrators and users:
- If you have a customer account with AnyDesk, change its password as a precaution and check whether 2FA can be activated.
- If passwords for permanent access are used for AnyDesk clients, change them as a precaution and use different passwords than for portal access at AnyDesk. This topic is likely to cause headaches, especially for supporters who roll out AnyDesk clients in large numbers to customers for remote maintenance and have provided them with an access password.
- Blocking access to all AnyDesk clients on the endpoints. This is likely to be the most tricky point, as on the one hand many scenarios will then result in functional restrictions. On the other hand, many users and administrators may not even know that AnyDesk clients are installed.
- Go through the access logs at AnyDesk in the logs and also on the endpoints (e.g. Windows) to see whether there have been any access attempts in the last 30 days that should not have taken place.
These are all quite general notes that require a lot of work, but are actually necessary – unless AnyDesk finally discloses more details so that it is possible to assess what is going on. Then the testing effort could possibly be limited.
Check whether AnyDesk is present on endpoints
What administrators should definitely do in my opinion, however, would be to search their systems for anydesk*.exe to determine whether any versions of the AnyDesk client have been included, possibly as part of an installed software.
Checks the client version for detections
When detections are made, check whether the client contains the latest version with digital signing by AnyDesk. However, there seems to be a lot of confusion here because clients supplied by OEM are still on version 7.x and are signed with a certificate from "philandro Software GmbH". However, there is a suspicion that the private keys for the certificate were lost during the hack. The client 8.0.8 for Windows is signed with a new certificate from AnyDesk GmbH – Bleeping Computer has published information on the details of the certificates here.
Decides whether the client may be executed
Once it has been clarified that the AnyDesk client is present on endpoints and which version it has, the decision is made as to whether a possible compromise could have taken place and whether an update is possible. In the case of an update, it is necessary to clarify which update options are available, whether the new version of the client is accepted by the endpoint security (some virus scanners already block the clients) and whether the new AnyDesk client version is still "trustable".
On the one hand, there currently seem to be technical problems with the update (mass of requests, certain things not working with custom clients, see the other parts of the article series). In addition, I received a number of messages from administrators over the weekend completely blocking the client from running for security reasons.
Articles:
AnyDesk confirmed, they have been hacked in January 2024, Production systems affected – Part 1
AnyDesk hack undercover – more information and thoughts – Part 2
AnyDesk hack undercover – Suspicious cases and more – Part 3
AnyDesk hack undercover – Access data offered for sale – Part 4
AnyDesk hack – A review – Part 5
AnyDesk hack – Review of the German CERT BSI report – Part 6
AnyDesk hack – Notes on exchanging certificates for Customs clients 7.x – Part 7
AnyDesk hack – more details (FAQ from Feb. 5, 2024) – Part 8
AnyDesk hack already noticed on December 20, 2023? – Part 9
AnyDesk hack confirmed as of December 2023; old certificate recalled – Part 10
AnyDesk hack: Revoke chaos with old certificates? – Part 11
AnyDesk hack: Newly signed clients available; what are your experiences? – Part 12
Similar article:
Störung bei AnyDesk, jemand betroffen?
AnyDesk: Be careful in using that remote support software